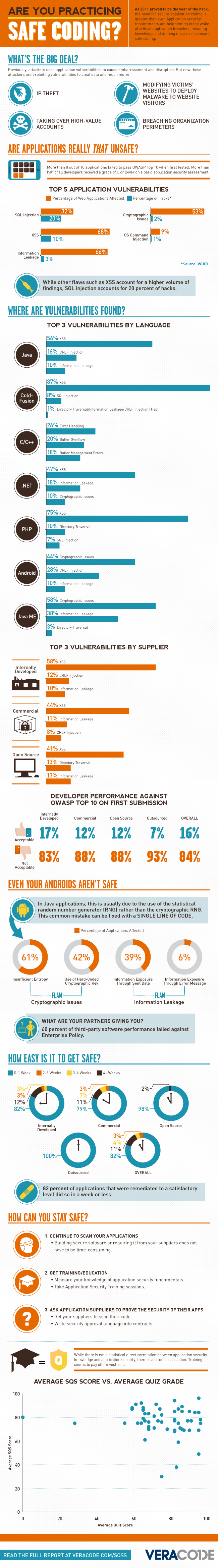
Are You Practicing Safe Coding
In 2011, hackers made a significant dent on the security of platforms, that year proved to be the year of the hack. As a result, there has been the need to increase the security in coding more than ever, and also to increase the emphasis on security of these applications.
What is the Relevance?
The trend is changing, previously, hackers made use of their techniques to cause disruptions with respect to system performance, but now, they are taking advantage of these platforms to steal data, money and classified information. Their activities can be summarized under the following headings;
• IP Theft.
• Taking Over Huge Accounts.
• Hacking into websites and introducing a malware.
• Breeching the security parameters of an organization.
Are Applications Truly Unsafe?
From a survey conducted, it was discovered that more than half of all application developers received a grade C and lower and in 10 applications, more than 8 failed to pass OWASP.
Here is a list of the top five application vulnerabilities.
1. For SQL Injection, 32% of web applications are affected while 20% of them are hacked.
2. For XSS, 68% of web applications are affected while 10% of them are hacked.
3. With respect to information leakage, 66% of web applications are affected while 3% of them are hacked.
4. For Cryptographic Issues, 53% of web applications are affected while 2% are hacked.
5.For OS command injection, 9% of web applications are affected while 1% are hacked.
Although other issues like XSS accounts for a higher volume of finding, SQL injections account for 20% of hacks.
Where Vulnerabilities Are Found
Based on programming language, here are the top 7 vulnerabilities.
1. Java Programming
– XSS forms 56%.
– 16% has CRLF Injection.
– 10% has Information leakage.
2. Cold Fusion
– XSS forms 87%.
– SQL Injection forms 8%.
– Directory Traversal/Information leakage/CRLF Injection forms 1%.
3. C/C++
– 26% has error handling.
– 20% has buffer over flow.
– 18% has buffer management errors.
4. .NET
– XSS forms 47%.
– Information leaks form 18%.
– Cryptographic issues constitute 10%.
5. PHP
– XSS forms 75%.
– Directory Traversal forms 10%.
– SQL injection forms 7%.
6. Android
– Cryptographic Issues forms 44%.
– CRLF injection forms 28%.
– Information leaks forms 10%.
7. Java ME
– Cryptographic Issues forms 58%.
– Information leakage forms 38%.
– Directory Traversal forms 3%.
Top 3 Vulnerabilities by Supplier
Here is a list of the top three vulnerabilities based on suppliers.
1. Internally Developed
– XSS forms 58%.
– CRLF Injection forms 12%.
– Information leakage forms 10%.
2. Commercial
– XSS forms 44%.
– Information leakage forms 11%.
– CRFL injection forms 8%.
3. Open Source
– XSS forms 41%.
– Directory Traversal forms 13%.
– Information leakage forms 13%.
Developer Performance Against OWASP
Acceptable Ratings
Internally Developed – 17%
Commercial – 12%
Open Source – 12%
Outsourced – 7%
Overall – 16%
Unacceptable Ratings
Internally Developed – 83%
Commercial – 88%
Open Source – 88%
Outsourced – 93%
Overall – 84%
Even Androids Are Not Safe
The safety of an Android based application is compromised by using a statistical random generation (RGN) instead of cryptographic RGN. This mistake can be fixed with a single code line. Here is the percentage of applications that were affected.
With respect to Cryptographic Issues, insufficient entropy forms 61% while the use of hard-coded cryptographic key forms 42%. With respect to information leakage, exposure of information sent forms 39% while exposure of information through error message forms 6% while with respect to enterprise policy, 60% of third party software performance failed.
How Easy is it to Remedy These Applications?
• For internally developed applications, 82% takes about a week to get safe, 3% takes about 3 weeks, 2% takes about 4 weeks while 12% takes about 4 weeks.
• For internally commercial applications, 79% takes about a week to get safe, 3% takes about 3 weeks, 7% takes about 4 weeks while 79% takes about 4 weeks.
• For open source applications, 89% takes about a week to get safe, while 2% takes about 4 weeks.
• For outsourced applications, 100% takes about a week to get safe.
• Overall, 82% takes about a week to get safe, 3% takes about 3 weeks, 4% takes about 4 weeks while 11% takes about 4 weeks.
On the average, 82% of the applications that were remedied to a safe level were remedied in less than a week.
3 Tips to Remain Safe
Here are some steps that will aid you remain as safe as possible.
1. Always scan your applications. It does not have to be time consuming building secure software.
2. Develop yourself by getting the right training. You need to develop your knowledge base with respect to security fundamentals.
3. Request the suppliers to prove that their applications have an excellent security level.
It is wise to invest in training with respect to security of application as it pays off in the long run. Invest in it.
Although millions of people visit Brandon's blog each month, his path to success was not easy. Go here to read his incredible story, "From Disabled and $500k in Debt to a Pro Blogger with 5 Million Monthly Visitors." If you want to send Brandon a quick message, then visit his contact page here.
